Ensuring that Kubernetes certificates are valid and not near expiration is essential for maintaining a secure and stable cluster. With PRTG Network Monitor, you can automate the monitoring of the Kubernetes API server certificate expiration date. Here’s a quick guide on how to set this up.
Step 1: Prepare the Monitoring Script
Check Kubernetes certificate expiration with the command below:
kubeadm certs check-expiration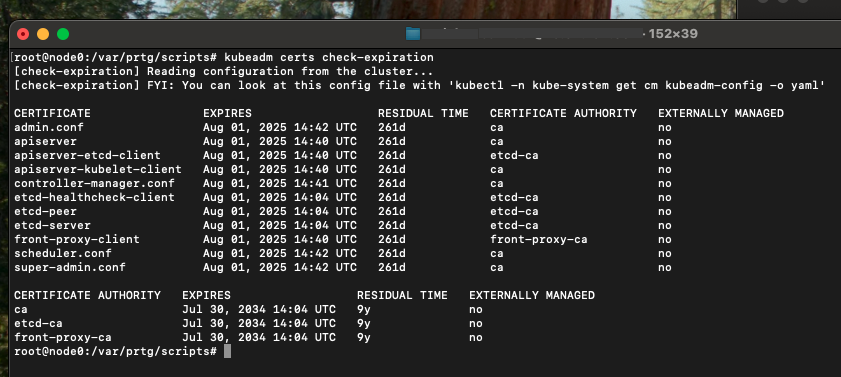
Create directory to store the script
mkdir -p /var/prtg/scriptsSave the following script as cert_mon.sh in /var/prtg/scripts. This script checks the expiration time of the API server certificate using kubeadm certs check-expiration:
#!/bin/bash
time=$(kubeadm certs check-expiration | grep '^apiserver ' | awk '{print $7}' | grep -o '[0-9]*')
echo "0:$time:OK"This script extracts the remaining days until expiration and outputs it in a format readable by PRTG.
Step 2: Make the Script Executable
Run the following command to make the script executable:
chmod +x cert_mon.shStep 3: Test the Script
To ensure the script runs as expected, execute:
./cert_mon.shYou should see the output indicating the residual days until expiration.
0:261:OKStep 4: Add the SSH Script Sensor in PRTG
- Go to PRTG and add an SSH Script sensor to the Kubernetes node.
- Point it to the
cert_mon.shscript. - Configure thresholds and notifications based on your monitoring policy.


And just like that, very simple, yet very useful script that will notify you when the Kubernetes API server certificate is nearing expiration, helping to prevent potential disruptions.