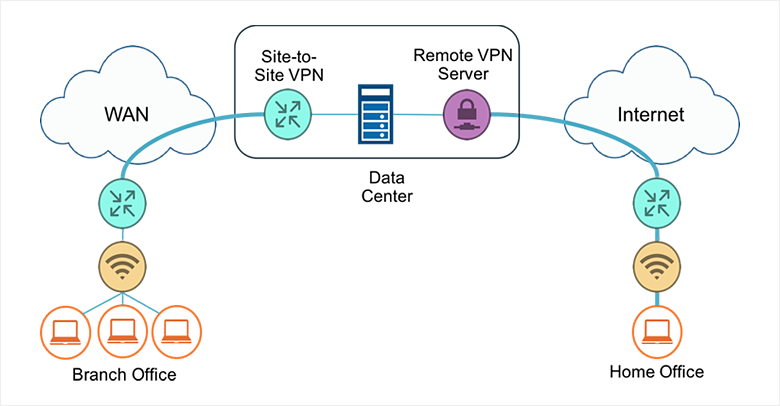
A Site-to-site VPN is a type of VPN connection that is created between two separate locations. It provides the ability to connect geographically separate locations. for example a linux server can be connected to a local computer behind a virtual private network in a remote office.
STEP 1: Install the VPN Tool
On server A, run to install strongswan:
Linux:
sudo apt install strongswan -y
STEP 2: Configure sysctl and iptables
cat >> /etc/sysctl.conf << EOF net.ipv4.ip_forward = 1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0 EOF
iptables -t nat -I POSTROUTING -m policy --pol ipsec --dir out -j ACCEPT
STEP 3: Backup Ipsec.conf and Ipsec.secrets for previous connections
Linux:
cp /etc/ipsec.conf /etc/ipsec.conf.bkup cp /etc/ipsec.secrets /etc/ipsec.secrets.bkup
STEP 4: Edit ipsec config
/etc/ipsec.conf
Paste the config below
It is very important that all the values match on both Linux and Cisco
config setup charondebug="ike 1, knl 1, cfg 0" uniqueids=no charondebug="all" conn vpn type=tunnel keyexchange=ikev2 aggressive=no authby=secret auto=add ike=aes256-sha1-modp1024 esp=aes128-sha1 ikelifetime=1440m left=LINUX_PUBLIC_IP_ADDRESS right=CISCO_PUBLIC_IP_ADDRESS rightsubnet=CISCO_SUBNETS dpddelay=300s dpdtimeout=120s dpdaction=restart rekey=no keylife=3600s closeaction=restart
keyexchange = ike | ikev1 | ikev2
method of key exchange; which protocol should be used to initialize the connection.
this value should match on both machines
esp = <cipher suites>
comma-separated list of ESP encryption/authentication algorithms to be used for the connection
ike = <cipher suites>
comma-separated list of IKE/ISAKMP SA encryption/authentication algorithms to be used
ikelifetime = 3h | <time>
how long the keying channel of a connection (ISAKMP or IKE SA) should last before being renegotiated.
STEP 5: Establish The Connection
After setting up, bring up the tunnel connection with the below command.
sudo ipsec up vpn # where 'vpn' is the connection name
Check the status of the connection with the following commands
sudo ipsec statusall sudo ipsec status
The output will be as below: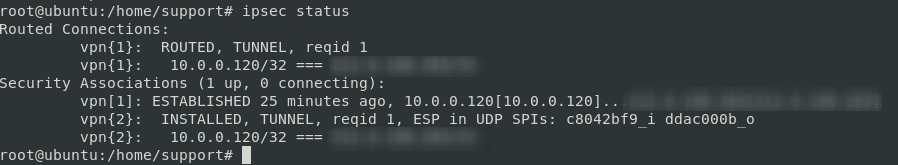 To restart ipsec , use:
To restart ipsec , use:
sudo ipsec restart
