Kubernetes is a powerful container orchestration platform that simplifies the deployment, scaling, and management of containerised applications. MicroK8s, a lightweight Kubernetes distribution, is a popular choice for development and testing environments. However, like any software, Kubernetes can encounter issues that need troubleshooting. One common problem you might face is dealing with expired certificates, which can disrupt your Kubernetes cluster’s operation. In this blog post, we will explore the error message:
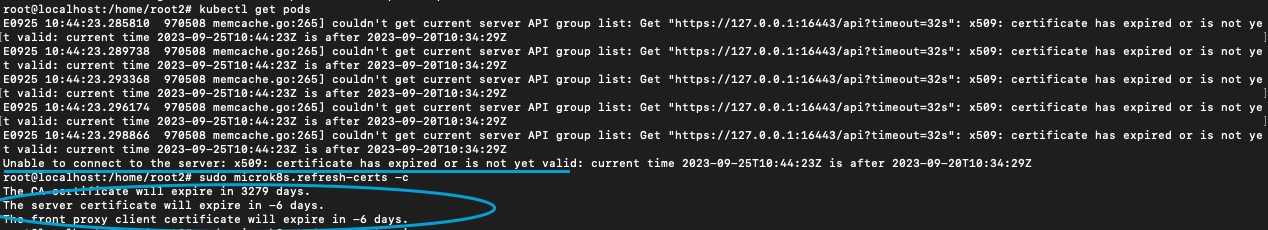
Unable to connect to the server: x509: certificate has expired or is not yet valid
Understanding the Error
The error message you’ve encountered suggests that the certificates used by your MicroK8s cluster have either already expired or are not yet valid according to the system’s current time. Certificates are a fundamental security component in Kubernetes, used for authenticating and securing communication between cluster components. When these certificates expire, it can lead to a breakdown in communication and ultimately disrupt the cluster’s functionality.
In your case, it appears that the server certificate and the front proxy client certificate have already expired, which needs immediate attention to restore the proper functioning of your MicroK8s cluster.
Resolving the Issue
To address the issue of expired certificates in MicroK8s, you can use the ‘microk8s.refresh-certs‘ command with the appropriate flags to renew the expired certificates. Here’s how you can do it:
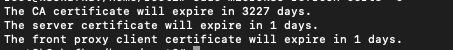
* Check certificate expiration dates with
microk8s refresh-certs -c1. Run the following command to refresh the server certificate:
microk8s.refresh-certs --cert server.crtThis command will generate a new server certificate, ensuring that your MicroK8s cluster has a valid and up-to-date server certificate.
2. Similarly, renew the front proxy client certificate using the following command:
microk8s.refresh-certs --cert front-proxy-client.crtRenewing the front proxy client certificate ensures that the components within your cluster can communicate securely.
After running these commands, your MicroK8s cluster should have refreshed certificates, resolving the issue of expired certificates. This should enable normal cluster operations without disruptions.
In Vanilla Kubernetes checking certificate expiration and renewing them is done with kubeadm command:
kubeadm certs check-expiration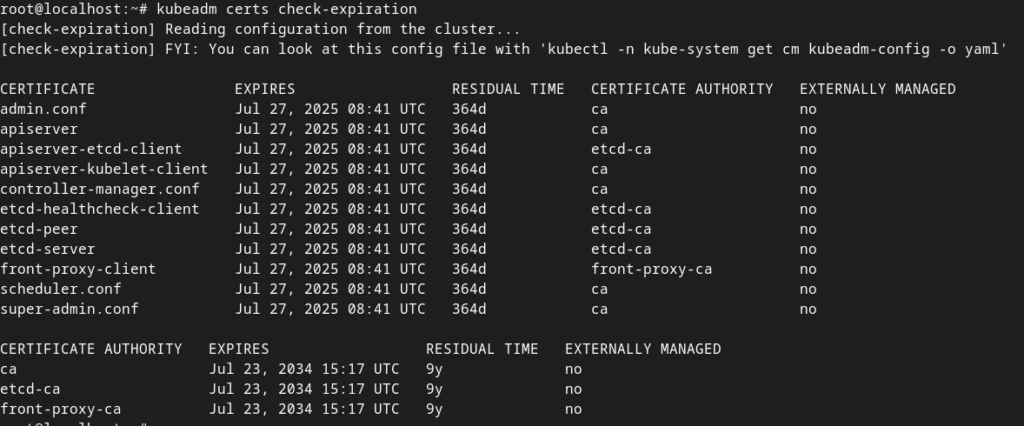
kubeadm certs renew all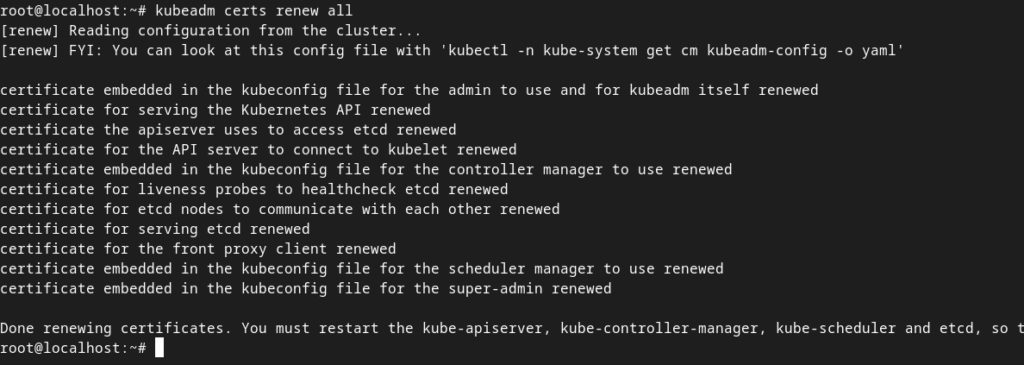
In a Kubernetes environment, certificates play a crucial role in securing communication between cluster components. When these certificates expire, it can lead to errors and disruptions in your cluster. In this blog post, we’ve discussed the common error message related to expired certificates in MicroK8s and provided a step-by-step guide on how to resolve this issue using the ‘microk8s.refresh-certs‘ command.
It’s essential to regularly monitor the expiration dates of certificates in your Kubernetes clusters and follow best practices for certificate management to ensure the continued security and stability of your environment. By promptly addressing certificate expiration issues, you can maintain a healthy and reliable Kubernetes cluster for your applications and services.